
Abstract
As a “new generation of value transfer Internet”, blockchain finance is not only the information transfer of the traditional Internet, but also the future value transfer network. The new world and value flow will be the pioneers, builders, leaders and successors of the future. “Aggregate the value flow wells of the new world to provide complete ETH mining applications for its services. It is the core business of DeFi Mining.”
DeFi Mining is a one-stop computing power mining platform. DeFi Mining is based on the computing power of mainstream digital assets (ETH), as well as mining machines and mining farms. Users can recharge to purchase computing power package mining income, and can also obtain investment returns by investing in the company's blockchain financial projects, thereby redefining the value of the ETH mining industry, and finally creating a centralized computing power service, financial service, and circulation service. A blockchain computing power mining financial service platform integrating information services.
Project Background Overview
1.1 Project Concept Background
Before the birth of Bitcoin, financial aggregation transactions around the world were realized through a centralized approach. However, with the development of internet technology, trading centres have more and more control over data, and the equality of trading individuals and trading centres in many aspects, such as the equality of trading, the transparency of information, and the reliability of historical information, is becoming more and more unequal. At the same time, data monopolies and data closures between the various centralized trading platforms have made it impossible for centralized institutions to do the same. DeFi Mining was born out of this situation and seeks to solve many of the problems of the current generation of financial services through new technology.
As a “new generation of value transfer internet”, blockchain finance is not only a traditional internet information transfer, but also a future value transfer network. The value flow of the new world will be the pioneer, builder, domainer and successor of the future. With Bitcoin and Ether breaking through the new highs in the past two years, the entire cryptocurrency market sentiment has also reached a high point, but from a microscopic perspective, the best performing pass-throughs in the DeFi space are only the leading projects in each segmentation track, and many investors who bought cryptocurrencies at high levels still have no hope of returning their capital. However, against this backdrop, some of those involved in liquidity mining have been able to earn high returns while preserving their capital, thanks to DeFi Mining, which uses an innovative structured risk-regulation mechanism and liquidity provisioning mechanism to attract additional investment from major chambers of commerce to provide pledged mining capacity for DeFi Mining crypto assets. Goal is to build a large ecology, i.e. to build a strong community and consensus before launching a product, i.e. a blockchain financial project, to enable users who already hold coins to sink in.
1.2 Mining has spawned a new industry chain
Secondly, mining as an infrastructure in the cryptocurrency world, it does not just exist in isolation. Cryptocurrency mining has evolved from CPU and GPU mining to ASIC mining, from individual mining to pool mining, and from no service at the beginning to perfect supporting services now. We can see through the whole evolution process of the mining industry that the cryptocurrency mining industry has spawned a new industrial chain around the development of the whole mining industry, from production equipment such as mining machines, mining farms and pools to logistics, accessories, finance and other supporting services have all emerged in response to the development of the mining industry and the rise in coin prices, thus enabling the entire mining industry to develop better.
1.3 The mining industry has huge room for development
The, as the cryptocurrency coin price continues to rise, its wealth effect will become more and more obvious, thus attracting more global users to actively participate. At the same time, it also drives the booming development of the entire cryptocurrency mining industry upstream and downstream. From the hosting of mining farms to the research and development of mining machines, from the technical optimization of mining pools to upgrading of logistics services, from the diversification of financial services to the introduction of new accessories, from the professional introduction of talents to the active layout of capital, all of them reflect the certainty and expansiveness of the future development of the entire mining industry.
1.4 Mining can effectively combat bull and bear market
The entire digital currency market experiences bulls and bears, peaks and troughs, and some industry participants, when experiencing industry bulls and bears, will choose between risk appetite and risk avoidance. And while mining sacrifices some liquidity relative to the high-risk, highly liquid digital currencies, its returns are also more long-term and stable.
Traditional mining problems
2.1 High investment requirement
At present, the mainstream mining form is still dominated by physical mining machines, which forces many users who want to mine to spend a certain amount of capital costs to buy a mining machine, after which they also need to build their own or find a suitable site for hosting, while the risk of the digital currency itself and the fluctuation of the coin price is relatively large. With so many uncertainties, users also need to pay a lot of capital and time costs in advance, thus raising the overall barrier to entry for the industry and discouraging many users.
2.2 Extensive knowledge required
Mining also has high professional requirements for miners, which involves two aspects: the professionalism of the hosting mine on the one hand, and the professionalism of the maintenance of the mining machines on the other. This is because a professional mining site has certain standards, whether it is the distance between machines or the ventilation and humidity of the site, which not only prolongs the life of the mining machines, but also allows them to run more stably. Maintenance specialisation requires professional maintenance staff who can deal with any problems that may arise with the mining machine, whether it is poisoning or hardware failure, thus guaranteeing that the mining machine is online 24/7.
2.3 Unregulated industry
As the current policy for mining and digital currency regulation is at a relatively early stage, legislation is lagging behind, and the overall development of the industry is in a state of barbaric growth, with a lack of unified standards, pre-sales and after-sales services, and varying levels of hosting, the industry is full of chaos, schemes and unspoken rules that give new and old miners headaches and even complaints.
2.4 Lackluster service
Mining is an industry with a large initial investment in fixed assets, and the financial services to match this are not perfect, resulting in poor liquidity of the fixed assets invested by miners. When miners need a certain amount of cash flow, they are stretched to the limit and have no way to liquidate their fixed assets in time to meet their financial needs, except for pledging and selling digital currencies. In addition to financial services, other services related to mining are also relatively backward, such as the construction and transfer of mining machine farms, the warranty and maintenance of mining machine parts, the reporting and publishing of mining information, etc., are all in a relatively rudimentary state.
Overview of DeFi Mining
3.1 Introduction to DeFi Mining
DeFi Mining is a global technology-leading ETH arithmetic mining cloud service platform, and an international website dedicated to providing global users with safe, convenient, reliable and innovative digital asset derivatives. DeFi Mining allows users to seamlessly switch between tokens on the chain in a fully decentralised and non-custodial manner. DeFi Mining is committed to providing global users with intelligent, secure, stable, fast and convenient digital asset investment and trading services, bringing intelligent new changes to global digital finance.
3.2 Product key elements
- Liquidity Mining
DeFi Mining supports single coin mining, pledged LP mining and transaction mining, and is completely decentralised. It can freely deposit tokens for exchange and can be freely withdrawn. It does not trade with other trading users, it trades with a pool of tokens and has an automatic market making model to calculate the trading price.
One of the features of DeFi Mining is that it pools everyone's liquidity together and then makes a market based on an algorithm. The AMM model is supposed to be one of the biggest innovations of the current bull market, the cryptocurrency market. AMM fundamentally changes the way users trade cryptocurrencies, unlike traditional order book trading models, where both sides of the trade interact with an on-chain pool of liquid assets. The liquidity pool allows users to seamlessly switch between tokens on the chain in a fully decentralised, and uncustodied manner. The liquidity provider, in turn, earns passive income through transaction fees, which are based on the percentage of their contribution to the asset pool. What's more, your assets remain in your personally controlled wallet and not into the trading platform, so they remain 100% safe.
- Trading and exchange type services
DeFi Mining wallets have built-in digital asset trading functionality, from wallets with access to centralised exchange platforms, such as BitPie, to wallets with access to decentralised trading platforms, such as Imtoken, to automated trading platforms with access to the Bancor mechanism, such as Tokenpocket. Some wallets offer a “flash exchange” function, where different currencies are exchanged at a certain “exchange rate”, often using a centralised exchange model for the backend of the currency exchange. This not only reduces the number of steps users have to take to transfer coins to other coins, reducing the probability of making mistakes, but also enhances user stickiness and provides a good development direction and capital deposit for the subsequent transformation of the wallet project. However, the built-in exchange greatly increases the complexity of the system and introduces greater risk for wallet products that require high security themselves, and the security of user funds will be challenged to some extent.
- News and information services
DeFi Mining has a wealth of built-in digital asset market information such as news feeds, market snapshots, project profiles, K-line charts, large capital flow monitoring, code activity and more. Blockchain project information and quotes are what pass holders need to keep up with the market, and are also a great entry point for gathering user traffic. A well-integrated information and quotes service in a wallet product will not only create enough stickiness for existing users, but also bring in more incremental users. However, information services require a certain amount of investment in human and financial resources, which can significantly increase the operating costs of the product. Currently, most wallets do not have a well-developed news and information service, and mainly focus on providing quotes.
- Money Management Services
DeFi Mining has a built-in wealth management module, which includes long-term fixed income, short-term flexible balance, digital asset P2P_financing and lending, and mortgages. At present, some of these finance modules are connected to third party services and do not participate in finance services themselves; some are finance products developed to provide cheap funds for the development of their own platforms, with the platform's earnings paying interest to users; some are digital assets raised by the platform and then invested in primary or secondary market transactions to obtain excess returns and pay interest to users; and some provide P2P digital asset lending and borrowing transactions. Others offer P2P digital asset lending and trading services, providing a matchmaking service between those who demand and those who provide assets. For long-term coin holders, digital asset management services hit the nail on the head and can be held to gain income, with annual yields ranging from 4% to 20% for various types of wallets. However, the blockchain industry is developing rapidly and the digital asset market is volatile, so financial products with poor liquidity will face greater risks. The digital asset finance market is currently immature and no industry benchmark leading companies have emerged. In addition digital asset P2P lending type, if it is difficult to control the risk of the lender, it is easy to cause default, please pay attention to the risk of investors.
- POS mining services
For blockchain projects that support the POS consensus algorithm, some wallets offer a lock-in to join the POS mining service, and the mining proceeds will be sent to users on a regular basis. Usually the master node for POS mining is provided by the wallet project side. Digital assets that meet certain capital requirements can participate in POS mining, with fixed lock time mining and also a mining model that supports redemption at any time. The wallet project side will take a proportional share of the mining proceeds, and both the wallet project side and the user can have a more stable additional income. The coins that currently support POS mining are: DASH, Lite Bitcoin, zCoin, Qtum and Hcash.
- Asset aggregation services
Usually users will hold different coins in multiple exchanges and wallets, which is not very convenient for centralized management and revenue enquiries. Such wallets can provide users with fund aggregation services, aggregating users' pass holdings in multiple wallets and exchanges through API interfaces, and platforms with poor support for API interface services can also use manual maintenance for initial input. Currently, the aggregation service can support exchanges, wallets, ICO funds and fiat funds.
Currently there are many different types of exchanges and wallets, each of which supports different types of digital assets, so users' funds are usually scattered across different platforms, which is not conducive to centralised management and queries. This type of wallet requires API interface development with many exchanges and wallets, and there are certain development and maintenance costs.
- IDO One-Stop Platform
DeFi Mining will establish a one-stop platform for IDO project evaluation, promotion and access, DeFi Mining adopts a community governance model, DeFi Mining's voting weight is the only measure, holding DeFi Mining is recorded as one vote, pledging DeFi Mining is recorded as two votes, the DeFi Mining re-purchased or pledged after the voting starts is not counted in the voting results. Provide traffic and support for project developers, data analysis and quality resources for customers. ido platform governance coins will also take liquidity mining mined out, involving specific economic models such as ido project mortgage, hitting new, buyback, etc.
- Other application products
The DeFi Mining team will continue to provide the latest products according to market development and demand. We strive to be the DeFi full traffic portal and provide the most complete DeFi products to serve our users.
3.3 Project solutions
- Lower the industry threshold and increase asset liquidity
DeFi Mining has lowered the entry barrier to the mining industry by giving fixed assets such as mining machines, mining farms and arithmetic power some liquidity in a platform-specific way, allowing more users who are interested in mining to participate and enjoy the benefits of mining without having to invest in expensive fixed assets. At the same time, it has also increased the liquidity of mining farms and miners' assets, enabling them to develop more rapidly.
- Scale and specialised expenditure costs
DeFi Mining will continue to build and purchase its own infrastructure and mining equipment, as well as cooperate with other ecological partners, in order to generate a certain scale effect, thus reducing the platform's procurement, construction and operating costs. At the same time, due to the large scale of the company, it will also have a relative advantage in obtaining the corresponding power resources and compliance qualification.
- Cross-currency mining services to enhance the freedom of mining
As the consensus algorithms of different coins are different, the required mining machines are also different, so this is a limitation to the freedom of miners. DeFi Mining can help miners to provide mining services for different coins under different conditions according to their individual needs, thus enhancing their freedom of mining.
- Empowering financial attributes to provide financial services to users
DeFi Mining will continue to expand its financial services and products to provide a full range of financial services and support to ecological members including miners, mining farms, mining pools and mining machine manufacturers to help them survive and develop better DeFi Mining and its partners will obtain the appropriate business licenses in accordance with local policies and regulations.
3.4 Advantages of DeFi Mining
- K-Chart: Once you enter the DeFi Mining platform, you can see the K-Chart by entering the contract address, which gives you a comprehensive and thorough view of the real changes in the ETH market. From the K-chart, investors can see both the trend of the bullion market and the daily fluctuation of the market conditions.
- Transparent trading: The model is simple, mainly aggregating transactions, and does not host the user's assets, eliminating the possibility of the exchange monitoring and stealing.
- Trading on the chain: The biggest difference with other ETH mining platforms is that DeFi Mining does all this through smart contracts, placing asset escrow, aggregated transactions and asset clearing on the blockchain.
- Highly trustworthy: Smart contracts are used to achieve a decentralized and trustless transaction mechanism, which solves the risk of internal operation, business ethics, asset theft and other risks that seriously affect the safety of users' assets due to human factors on centralized platforms.
- Security and efficiency: Users' assets can be transferred freely without any approval, and there is no need to worry about hackers stealing or losing coins, so there is sufficient security.
3.5 Value services
- Calculating power service
DeFi Mining is based on ETH mining machines, mining farms and the arithmetic power behind them. Arithmetic services are the core and most fundamental business of DeFi Mining, and users can enjoy a wide range of arithmetic services through the platform. In the world of cryptocurrencies, apart from buying and selling cryptocurrencies through exchanges, the only way to mine cryptocurrencies is to have arithmetic power, so the value of arithmetic power is particularly important here. Once a platform user has arithmetic power, they can turn it into tangible revenue through arithmetic power. DeFi Mining users who use the platform to purchase arithmetic for mining services will see their daily earnings increase as the price of the cryptocurrency rises, and vice versa.
Therefore, DeFi Mining itself has the ability and demand to continuously extend its cooperation with external arithmetic power, and as the arithmetic power purchased by DeFi Mining and accessed by external parties continues to increase, the larger the scale, the more users will continue to increase.
- Streaming Service
DeFi Mining's miners can transfer their fixed assets, such as mining machines and mining farms, through the platform under certain conditions within the platform and on the secondary market, thus increasing the liquidity of miners' assets and allowing more idle arithmetic power to come into play, so that users who want to mine can participate in the process. As DeFi Mining grows, the platform will gradually increase the amount of arithmetic purchased by the platform and the amount of external arithmetic. Users can purchase physical ETH miners from DeFi Mining or transfer their own miners to our mine for management
- Financial Services
As one of the core services provided by DeFi Mining, we will provide cryptocurrency_users with financial services such as collateral lending, hedging, coin-flash, asset management, leveraged instalment, OTC, option contracts, etc. Cryptocurrency will be used as a payment tool for DeFi service fees. DeFi Mining will continue to improve its financial services and derivative products according to market conditions and the needs of cryptocurrency users.
- Information Services
The mining industry has experienced many years of development, but the information in the industry is still relatively closed and asymmetric. From local electricity prices to the sale and purchase of mining machines, from industry blacklists to industry resource information, the mining community lacks an authoritative and systematic information release and sharing platform. In the future, DeFi Mining will gradually integrate the industry's leading organizations into the entire ecosystem, so that miners can take the easy way out and get access to reliable resources and information from the platform. The information service scope mainly includes network information release, mining machine sales, mining machine reviews, etc.
3.6 Core of DeFi Mining
- Transparent transactions: The model is simple and mainly deals with aggregated transactions, and does not host users' assets, thus eliminating the possibility of the exchange monitoring and stealing.
- Transaction on the chain: DeFi Mining all of this is achieved through smart contracts, the asset custody, aggregation transactions, asset liquidation are placed on the blockchain.
- High trust: Smart contracts are used to achieve a decentralised and trustless transaction mechanism, which solves the risk of internal operation, business ethics, asset theft and other risks that seriously affect the safety of users' assets due to human factors.
- Security and efficiency: Users' assets can be transferred freely without any approval from anyone, and there is no need to worry about hackers stealing or losing coins, so there is sufficient security.
3.7 Cornerstone of DeFi Mining
- Engineering-level development capabilities
DeFi Mining community members have unique insights and experiences in blockchain technology. They have many years of development experience, which gives DeFi Mining's technology development a huge advantage and guarantee. DeFi Mining already has a decentralised application in internal testing, the creation of which comes from the contributions of community volunteers and the assistance of the founding team.
- Composite core business logic
DeFi Mining has core business segments covering all directions, with developments in information sharing, information settlement systems, multi-functional wallets, traceable elements, smart_contracts and other areas, which will eventually converge and link into an overall cryptocurrency trading ecosystem.
- The industry's first-tier cooperation institutions
Excellent partners are the foundation of success. DeFi Mining has top-tier partners around the world, who will cooperate with DeFi Mining in all aspects and help DeFi Mining at all levels to promote its rapid development.
- Simultaneous launch of the global market
DeFi Mining has a rich community base and user base, and has been commercially deployed globally. At the same time, strong alliances allow DeFi Mining to launch simultaneously in various markets around the world, seizing opportunities and expanding markets in time!
In the future, DeFi Mining will establish multiple user communities and venues in Spain, Canada, USA, Singapore, Northern Europe, Eastern Europe, Japan, China, Korea, Australia, Malaysia, Cambodia, South America and other countries and regions to accelerate the project's development.
- Cutting-edge industry trends
DeFi Mining enables the existing cryptocurrency trading market to gain disruptive changes and establish an advanced and unique payment ecology. It is hoped that a series of open and fair rules and standards will promote rapid changes in the entire market, optimise the current industrial structure, rationalise the allocation of public welfare resources, and ultimately realise the decentralised ecosystem established by the DeFi Mining protocol based on blockchain technology.
- Global commercial application
In order to realize DeFi Mining's ambitious ideals and mission, DeFi Mining will make use of its advantages to land commercial applications globally, actively cooperate with various traditional industries to help the development of the blockchain crypto industry, improve its influence and establish an ecosystem led by DeFi Mining.
DeFi Mining Technical Architecture
4.1 DeFi Mining System Architecture
The DeFi Mining system has six layers, namely the data layer, network layer, consensus layer, incentive layer, contract layer and application layer.
- Data layer
Based on the high redundancy storage mechanism of the blockchain, blockchain storage has a certain impact on the scalability and performance of the blockchain. The DeFi Mining framework is designed with a multi-layered node system, and different storage strategies (distributed bookkeeping) are selected according to different node applications.
- Network layer
The P2P Protocol supports data transmission and signaling exchange among nodes in the blockchain network and is an important communication guarantee for data distribution or consensus mechanism. The DeFi Mining system is designed to support multiple P2P protocols, communication mechanisms and serialization mechanism configurations, so that flexible protocols can be used according to different scenarios. In terms of communication security, HTTPS, TLS, WSS (SecureWebsockets) and other protocols are flexibly supported, and OAuth authentication integration can be extended to support the external service interface of the platform application.
- Consensus layer
DeFi Mining (delegatedByzantine Fault Tolerance) consensus algorithm, expanding the underlying network consensus algorithm, with high performance, high consistency characteristics, suitable for financial payments, digital transaction data frequently generated, and a high degree of real-time bookkeeping requirements of weak central upper layer applications.
- Incentive Layer
DeFi Mining not only has an airdrop for genesis consensus rewards, but also a liquidity mining pool for long-term network value maintenance. Because of DeFi Mining's unique consensus mechanism, anyone can join at any time to earn rewards.
- Contract Layer
For each smart contract submission, deployment, use and cancellation of a complete and controllable process management, and integrated rights management mechanism for comprehensive security management of the mechanisms of smart contract operation.
- Application layer
The application layer will provide a common transaction protocol, support multi-language integration and functional expansion, with support for Java, JavaScript, Python and other languages, and has been fully applicable to the underlying network expansion.
4.2 Arithmetic time-sharing system
DeFi Mining's arithmetic services are provided by the platform's own machines and external organizations that generate arithmetic 24/7. Users can freely choose when they want to use arithmetic, the amount of arithmetic and the corresponding mining coins through the platform, which improves the efficiency of arithmetic usage and breaks the inconvenience of mining caused by the limitation of firmware facilities in the past.
4.3 Trusted Proof of Stake Consensus (TDPOS)
The DeFi Mining platform uses Trusted Proof of Stake Consensus (TDPOS), a secure and trusted consensus protocol with high robustness and flexibility. Compared to traditional consensus mechanisms, TDPOS ensures a reliable source of distributed data through a hierarchical trusted consensus and hierarchical auditing strategy, safeguarding the fair rights and data privacy of participating nodes, while the transaction performance of over 1 million TPS is fully capable of handling a high concurrency sharing ecology.
We define the hierarchical Trusted Consensus (PT) of TDPOS as a function of Proof of Identity (PIA), Proof of Compliance (PCO), and Proof of Credit (PCR): PT=F{f(PIA),f(PCO),f(PCR)} and the three hierarchical credible proofs containing documents or transaction acts are described as follows.
Proof of equity (PIA): the higher the number of nodes locking coins, the higher the score. Proof of Compliance (PCO): is to verify the transaction behavior with the corresponding organizational policy and legal code requirements. Proof of Credit (PCR): is a dynamic credit verification that identifies the transaction behaviour on the role chain.
Combined with the decentralized features of the blockchain system, we incentivize the release of transaction behaviors with high credit consensus through the layered credit management and TOKEN mechanism of TDPOS with layered trusted consensus, which can greatly reduce the cost of information screening for the roles in the ecology, while improving transaction efficiency and guaranteeing transaction security.
4.4 Technology Applications
- P2P communication
P2P is the core foundation of blockchain, with features such as decentralization, scalability, robustness, privacy and high performance. The block is linked to DeFi Mining's loT devices and users, and is deeply optimised in terms of session maintenance, address determination, communication mechanism, storage scheme, transaction payment, etc. By specifying the physical configuration and size of the user and consensus nodes, and adopting a sharding mechanism and high-speed network connection, the communication, computation and storage burden of the consensus nodes is reduced and the transaction performance of the blockchain is improved, thus achieving the maximum performance of blocking for loT devices and providing the foundation for the registration, digitization, authentication and security of IoT devices in the future.
- DeFi Mining encryption algorithm
The encryption and decryption of information is the key link of blockchain, mainly the algorithm of hash function and asymmetric encryption.
(1) The hash function part, currently there are mainly SHA, MD5 and other algorithms, and also includes the use of algorithms in series and in parallel. Since commercial applications generally focus more on performance issues, the DeFi Mining base algorithm is mainly the SHA256 algorithm.
(2) Asymmetric encryption part, there are mainly asymmetric encryption algorithms including RSA, DSA, elliptic curve algorithms, etc. Blockchain generally uses elliptic curve algorithms, including ECDSA and SCHNORR, considering that the verification speed of Schnorr signature is faster than ECDSA signature, and the size of this signature can be smaller, and also natively supports multiple signatures. This is in line with the small size of the Internet of Things, so DeFi Mining has developed its own SDSchnorr algorithm based on Schnorr.
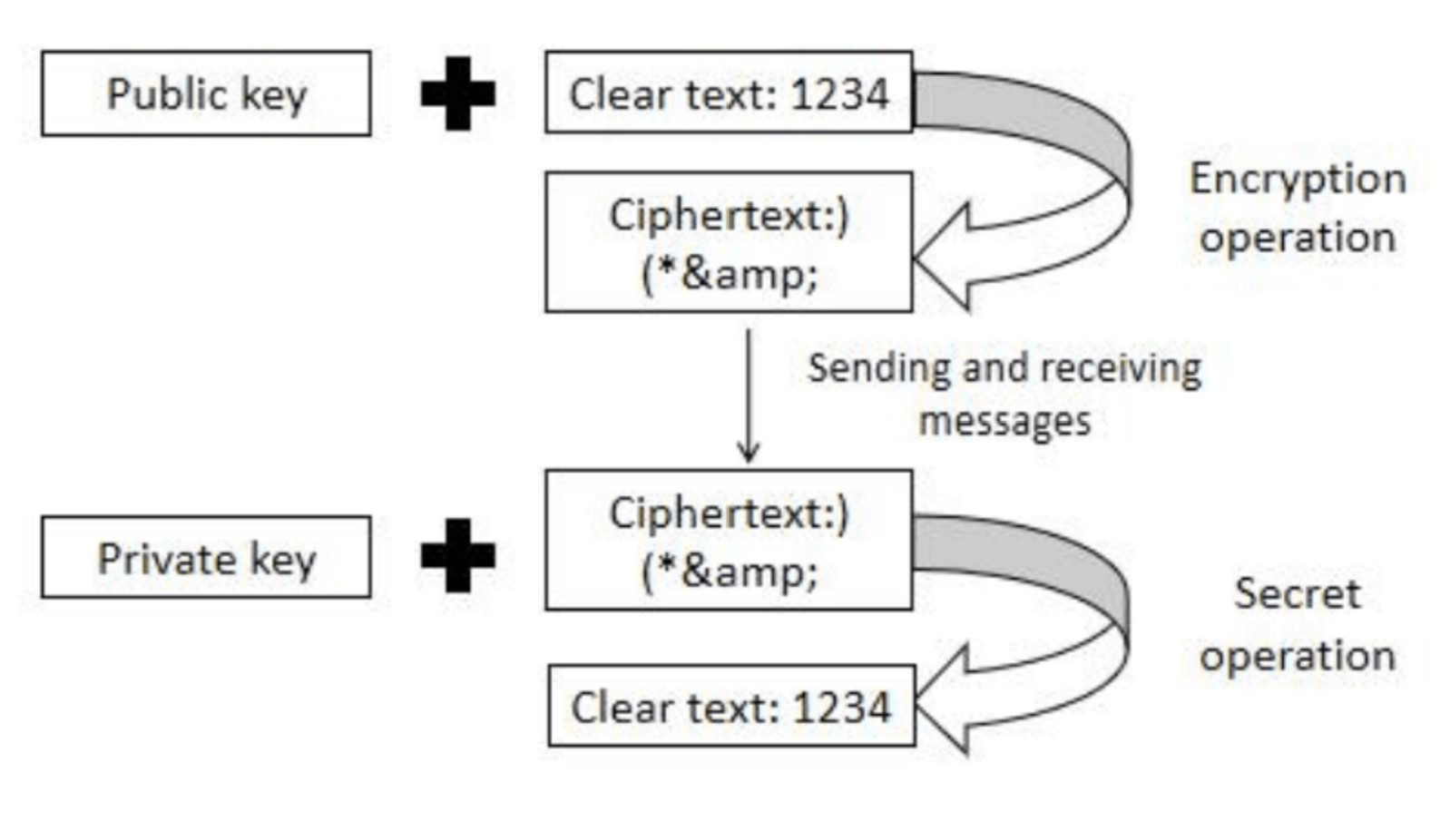
At the same time, DeFi Mining has abstracted the underlying cryptographic algorithm library and interchangeable channels for the algorithms to meet the algorithmic and security needs of different loT applications. The names of the wallet and the address are interchangeable in the underlying block.
- DeFi Mining Smart Contract
Each Internet-accessible lot device is given an “identity” on the blockchain and has a globally unique identifier that can be used to identify a credit identity. Each smart contract has a unique public address, just like a normal wallet. The difference is that the smart contract's private key is discarded when the contract is created, so no one can send the digital assets inside the smart contract after it is created, except for the consensus mechanism. For the lot's monitoring event-based up-chaining needs, i.e. the loT device holder sets the smart contract, data storage path and data accounting amount in advance, it can be broadcasted across the network as well as stored in digital records. In the event of a relevant abnormal event that is incorporated into the blockchain's supervision, DeFi Mining's smart contracts require mandatory, strong real-time and fully automated triggering. The data for triggering conditions is also blockchain-protected data, which is accurate, safe and secure, and cannot be tampered with.
- Cross-chain communication protocol
DeFi Mining supports cross-chain asset exchange protocols, which are extensions to existing asset exchange protocols, allowing multiple participants to exchange assets on different blockchains, and guaranteeing that all steps in the entire transaction process are all steps of the transaction are guaranteed to succeed or fail. At the same time, the cumbersome process of exchange via an exchange is eliminated. The flexibility of payment methods will stimulate a certain degree of diversity among users.
- 5G cloud storage
DeFi Mining 5g storage provides a special storage mechanism, which can not only prevent the storage of duplicate data, but also ensure the same security, break the “common sense” of the industry, and achieve both fish and bear. When using this mechanism, in addition to the user permission table, a global metadata table should be maintained to record the corresponding relationship between plaintext hash and ciphertext hash. When writing data, you should first query whether there is the same hash data, and if there is no such item, save it again.
- Hash (data) → hdata to calculate plaintext hash
- If checkdup (hdata) = true goto 11, if the same data already exists, go to step 11
- The symmetric key is randomly generated by randomsym () + STK as the file storage key
- Enc (STK, data) – encdata encrypt files with storage key
- Hash (encdata) – henc to calculate ciphertext hash
- The symmetric key is generated from the plaintext of the data by genkey (data) → sData
- After adding salt, hash value is calculated. The reason for adding salt is that plaintext hash is a public value. If 5g storage blockchain is not added salt to enable partial storage, people who do not have plaintext data can also obtain the key. In order to ensure consistency, the salt value can be a fixed value.
- Enc (hdata, STK) - encstk'encrypts the storage with the symmetric key generated by the data plaintext
- Store the key. This is a very “weird” step. It uses plaintext as the key and the key as plaintext to encrypt. When most people look at this algorithm, they think it is reversed. In fact, it is specially designed in this way, and this step is the core step of de duplication after encryption.
- Putipfs (encdata) stores encrypted data into IPFS
- Putmeta (hdata, henv, encstk) stores 'encrypted ciphertext hash and plaintext
- The key is recorded in the global metadata table and in the plaintext hash key
- Goto 14
- Get meta (hdata) henv, encstk'get ciphertext from global metadata table
- Storage key after hash and plaintext encryption
- Genkey (data) → sData uses the same algorithm to generate symmetric key from data plaintext
- The symmetric key is used by Dec (sData, encstk ') - STK to decrypt the storage key
- Enc (spub, STK) – encstk uses the user's encryption public key to encrypt and store the key
- Putpri (hdata, encstk) stores the encrypted storage key of the encrypted public key to the user
- The user permission list is recorded under the clear text hash item
- When getting data, take out the corresponding ciphertext hash from the plaintext hash in the global metadata table, take out the ciphertext hash from the IPFs through the ciphertext hash, take out the encrypted storage key from the permission list, decrypt the encrypted storage key with the user's encryption private key to obtain the storage key, and decrypt the encrypted data with the storage key to obtain the data plaintext.
- It is obtained by getmeta (hdata) → henc from the global metadata table through plaintext hash
- The ciphertext hash getpri (hdata) → encstk obtains the encrypted public key from the permission list through plaintext hash
- Get IPFs (henc) → encdata extract ciphertext from IPFs with ciphertext hash
- Dec (sprv, encstk) STK encrypts the user's public key with the user's private key
- The encrypted storage key is decrypted to obtain the storage key
- Dec (STK, encdata) - data decryption to obtain file data
- The optimized DSN scheme not only effectively guarantees the security of data, but also realizes encryption and de duplication. In order to achieve better de duplication effect, the data can be divided into blocks according to a fixed length, and each block is de duplicated separately. The above scheme can only be used to store static data. When storing dynamic data, not only the ID that does not change with the content should be used to replace hash as the identification of data, but also the verification of write permission should be added to prevent the data from being covered and tampered by others.
- The creation process is as follows:
- Xun randomasm () - swpub, SwPrv randomly generates asymmetric key as write permission key
- Create (swpub) - ID creates a dynamic data, obtains a unique ID, and records the public key of the write permission corresponding to the ID
- Random sym () - STK randomly generates symmetric key as storage key
- Enc (spub, STK) – encstk uses the user's encryption public key to encrypt and store the key
- Putpri(ID, encstk) stores the encrypted storage key of the encrypted public key into the user permission list, and records it under the ID. the process of each data writing is as follows:
- Get pri (ID) + encstk to retrieve the encrypted storage key from the user permission table
- Dec (sprv, encstk) → STK encrypts the user's public key with the user's private key • The storage key is obtained by decryption
- Enc (STK, data) → encdata encrypt files with storage key
- Hash (encdata) → henc to calculate ciphertext hash
- Enc (SwPrv, henc) - enchenc uses the public key of the ID's write permission to hash the ciphertext autograph
- Putdyn (ID, encdata, enchenc) writes encrypted dynamic data to sign data
- Write authorization on behalf of. When a node storing dynamic data fragments writes dynamic data, it needs to verify the write permission first
- Get key (ID) → swpub get the public key of write permission corresponding to the ID
- Hash (encdata) - henc to calculate ciphertext hash
- If Dec (swpub, enchenc) = henc write (encdata)
- The reading process of writing dynamic data is as follows:
- From the permission list, getpri (ID) — encstk obtains the data encrypted with the encryption public key corresponding to the ID
- Storage key
- Get dyn (ID) – encdata read ciphertext from dynamic data storage area with ID
- Dec (sprv, encstk) - STK encrypts the user's encrypted public key with the user's encrypted private key
- The encrypted storage key is decrypted to obtain the storage key
4.5 Technology Applications
DeFi Mining is a secure and reliable platform that combines on-chain and off-chain innovation through technical and conceptual innovation.
- Password setting for device use
Users can be reminded to set unlocking passwords, unlocking gestures or fingerprint unlocking, wrong password unlocking time period, high strength of device transaction password, if there is no perfect password setting control, it can not be directly accessed to view personal privacy information after the loss of the device, to conduct transactions.
- Create a wallet keyword security
The private key process is secure and can be saved locally.
- Transaction process security
You can display the address of your account and verify whether the address has been modified, so that your money is not lost.
- Data storage security
Data can be stored on the storage device, including the private key storage method, stored on the device memory card, which can be accessed externally, to improve the relevant function design, to protect the relevant data from hacking.
- System integrity security
The ability to verify the strict integrity of the equipment system, to check whether it is genuine and to prevent tampering by hackers or attackers in the place where the equipment is distributed.
The DeFi Mining Ecosystem
5.1 DeFi Mining Industry Chain
With the continuous development of DeFi Mining, the number of organizations that will reside in the DeFi Mining platform will also increase, and eventually a diversified ecosystem will be formed that includes exchanges, mining pools, mining machine manufacturers, social media, hot and cold wallets and mining services. Users holding cryptocurrencies will also enjoy certain rights and benefits when they access the main chain, such as discounted exchange fees, discounted mining pool fees, discounted mining machine purchases, priority purchase rights, purchase installments, token purchase rights, cold wallet benefits, etc. DeFi Mining will cooperate with more eco-system institutions through the main chain to give more rights and value to cryptocurrencies. DeFi Mining will cooperate with more eco-system institutions through the main chain, thus giving more rights and values to the cryptocurrency
5.2 DeFi Mining Wallet
To facilitate the use of the wallet by ordinary users, the DeFi Mining wallet uses the SPV method, i.e. accessing the wallet through the web. Cold wallets are suitable for wallets with large sums of money, where the public and private key pairs are generated offline and the user can generate any key pair they like. Hotwallets: Hotwallets are suitable for small and fast transaction scenarios. Hotwallet keys are hosted in a way that when a user registers for a wallet account, the private key generated using the user's payment password pair is encrypted locally on the user's computer via 3DES and the encryption results are hosted in the wallet cloud via the SSL protocol. This means that the hot wallet key information transmitted over the network and stored in the cloud is the user's encrypted data and no one other than the wallet user has access to the original content of the private key.
When a user needs to sign a transaction, the private key is obtained from the wallet cloud server and the content is decrypted on the user's local computer by the user entering the payment password, and upon successful decryption, the local wallet program will sign the transaction information with the private key and submit it to the DeFi Mining wallet network for trading. The DeFi Mining wallet also contains two types of assets - native assets and registered assets - similar in nature to real-life wallets that contain Chinese Yuan and various cards. Native assets can be used without any trust, while gateway-registered assets must trust the corresponding assets in order to exchange value.
Based on the above, and in order to better build the DeFi Mining wallet ecosystem, the DeFi Mining wallet introduces a series of key pairs, so that each wallet address corresponds to a key pair: a private key and a public key. The private key is a random number generator to generate a 256-bit entropy, displayed as a 64-bit hexadecimal number, which is unpredictable and unrepeatable, and therefore unique. It holds the ownership and control of the wallet and is used to sign and verify each transaction. In order to lower the user's threshold, the mnemonic becomes another manifestation of the plaintext private key. The DeFi Mining wallet, in order to help users to memorise complex private keys and increase convenience, generates a public key through a certain cryptographic algorithm (e.g. a hash function), which corresponds to the private key one by one. Its centralised wallet: a smart wallet for personal digital assets that supports the storage and transfer of a wide range of token transactions, will play a vital role in the next generation of the Internet digital economy. It can track and capture the data and market analysis of each exchange in real time, carry out intelligent arbitrage transactions in real time, determine the price difference of each trading platform and the trading volume of each currency to decide whether to carry out arbitrage tasks, and initiate transactions at the right time by itself, combined with a variety of arbitrage methods can be completely unaffected by price increases and decreases. The combination of multiple arbitrage methods can be completely independent of price increases and decreases. It solves all the drawbacks and risks of manual arbitrage.
5.3 Crypto Asset Trading System
The DeFi Mining Crypto Asset Trading System is a user trading platform. All users can convert multiple assets within the platform, where digital assets are a distributed peer-to-peer network system. As such, there is no 'central' server and no central control point. The Digital Asset protocol includes a built-in algorithm that regulates the mining function in the network. The task that miners must complete is to successfully record a block transaction in the digital asset network. This difficulty is dynamically adjusted. Digital Assets before Digital Assets represents the culmination of decades of cryptography and distributed systems, a unique and powerful combination that brings together four key innovations. Digital Assets consists of these:
- a decentralised peer-to-peer network (digital asset protocol)
- a public ledger of transactions (blockchain)
- a decentralised data and deterministic asset issuance (distributed mining)
5.4 DeFi Mining financial platform
Contract escrow platform, risk avoidance and stable returns. Cryptocurrencies are naturally decentralised, and most hot wallets inherit this property. As the private key is held by the user, it cannot be recovered if lost and transactions cannot be rolled back, thus putting the “wallet security awareness” of many users to a great test. DeFi Mining is the world's first and only personal digital wealth management product that combines multi-currency, cross-chain, decentralised trading, P2P encrypted instant messaging and integrated social community applications.
Lending and financial gains: DeFi Mining will later launch a one-click aggregated lending service to expand the underlying assets for lending and insurance, enhancing the liquidity of users' assets. The aggregation of mainstream and today's most popular major Defi lending platforms, such as MakerDao, Compound, etc., will reduce users' borrowing costs by adjusting the choice of coin weights and minimum interest rates in real time. It also connects off-chain credit behaviour with on-chain financial behaviour based on a credit prophecy machine. Users with a good credit history can also use their “credit behaviour” record to participate in behavioural mining, and DeFi Mining may even have the attribute of mining weighting in the future.
Project Development Planning
| Time | Development Planning |
|---|---|
| August 2021 | Complete development and design of the prototype based on the DeFi Mining platform |
| September 2021 | Beta version of DeFi Mining platform goes live for testing |
| November 2021 | DeFi Mining platform goes live in beta |
| December 2021 | Applications go live, integrate many industries, organise multilingual platforms for global business synergy operations and create a trillion dollar DeFi Mining infrastructure platform |
| March 2022 | DeFi Mining has contacted more overseas blockchain exchanges to actively promote overseas DeFi Mining launch plans and enhance the international reach of the DeFi Mining public project |
| June 2022 | Collaborate with more developers on more types of mining projects |
| 2023 | Complete global membership roadshow marketing |
Summary
The wheel of historical development rolls forward, and the development of society is changing day by day. Blockchain finance can contain everything, and the trend development has become irreversible. Whether we are pioneers or watchers is the most significant choice you can make in this era.
DeFi Mining platform: will give the future financial flow of the ETH world a best entrance and base. We will be the navigator, pathfinder, domainer, discourse, technology benchmarker and ecological city pool of the blockchain financial world.
We are not just involved in DeFi Mining, we are involved in building the entire ETH world. We are at the forefront of the new world, we reap the scenery and the territory. At the same time, the success of DeFi Mining is driven entirely by the consensus of the community members. Let's build the brilliance and legend of DeFi Mining with the best product and the strongest consensus.
Arbitrage Rules
In order to maintain the transparent, stable and fair operation of the mining pool, the members of the mining pool must abide by the following arbitrage rules:
- Strictly abide by the membership agreement of the mining pool And recycling rules, handling fees, etc. Any violation of the agreement is illegal and will be severely punished.
- It is forbidden to use information asymmetry for arbitrage. The members of the mining pool are prohibited from using the information asymmetry of other members to conduct internal transactions or use information for personal gain. If there is such a situation, severe penalties will be imposed according to the circumstances.
- Carefully review the application for release and recycling Mining pool members must carefully review the application for release and recycling of miners, especially large-value applications. If any suspicion of arbitrage is found, it must be reported to the mine pool manager immediately and necessary measures must be taken.
- It is forbidden for mining pool members to send USDT to each other for arbitrage. It is forbidden for mining pool members to send USDT to each other for arbitrage. If it is found that there is an arbitrage behavior among the members of the mining pool by sending USDT to each other, severe punishment measures will be taken depending on the situation.
- Prohibition of malicious manipulation of the market Any form of malicious manipulation of the market among members of the mining pool is prohibited, including but not limited to false propaganda, short-term trading using ETH price fluctuations, etc. If such behavior is found, corresponding punishment measures will be taken in accordance with laws and regulations.
- Strictly abide by the risk control principles Mining pool members must strictly abide by the risk control principles, including but not limited to diversification of investment, rational allocation of mining machines, risk reduction, etc., to ensure the safety and robustness of the mining pool. If there are excessive risk-taking and bad risk control behaviors, it will cause disputes and disputes among mining pool members.
- Establish a sound regulatory system In order to ensure good cooperation, mutual supervision and self-discipline among mining pool members, especially for potential arbitrage in various transactions, a sound regulatory system needs to be established. The mining pool management department should be responsible for implementing the supervision system and ensuring the strict implementation of the rules. To sum up, the members of the mining pool must establish an honest, fair, transparent and cooperative relationship, and strictly abide by the arbitrage rules to maintain the stability and security of the mining pool.
Liquidity Mining Pool Rules
Dear mining pool users: In order to protect the rights and interests of all users, we have formulated the following liquidity mining pool rules:
- Exchange USDT for ETH when airdrop rewards are prohibited. USDT cannot be exchanged for ETH, even if the transaction is profitable.
- Pool members are not allowed to send USDT to each other for arbitrage. If it is found that the members of the mining pool conduct arbitrage by sending USDT to each other, severe penalties will be imposed depending on the situation.
- If we find users who violate Rule 1, we will take some punitive measures, mainly including the following aspects:
- Deduct the corresponding reward air investment qualification amount;
- For users who have repeatedly violated or maliciously violated the regulations, we will prohibit them from entering the mining pool;
- If the circumstances are serious, it will be eliminated naturally, the mining pool will be eliminated, and all qualifications for reward airdrops will be deducted.
- After the prohibition period of Rule 1 expires, we will restore the user's USDT amount and deduct the corresponding transaction fee. At the same time, the assets of violating users will be frozen and deducted from the reward air investment qualifications.
Note:
- There may be special circumstances, special conditions or changes in the implementation of these rules. We will notify the mining pool users in advance and publish it in an announcement or other appropriate ways.
- If you do not abide by the rules of the mining pool, your rights and interests may be damaged. Please proceed with caution.
- We are committed to maintaining the fairness and transparency of the mining pool, and hope that all users will jointly maintain the stable operation of the mining pool. The above are our mining pool rules, please familiarize yourself with them as soon as possible, and jointly maintain the smooth progress and final results of our mining pool. If you have any questions or suggestions, please feel free to contact our service staff.